This is the first in a multi-part series that will focus on the growth, investment, and M&A trends in the blockchain and cloud storage industry.This first report on the blockchain and cloud storage industry will be a high-level introduction to the industry. We will examine some of the technologies involved and current market players.

Over 1,500 online data breaches occurred in 2017, exposing close to 180 million records, with numbers expected to rise[1]. The encryption, distribution and immutability of blockchain cloud storage provide an alternative to traditional cloud storage that may increase data security.
A Combination of Blockchain and Cloud Storage
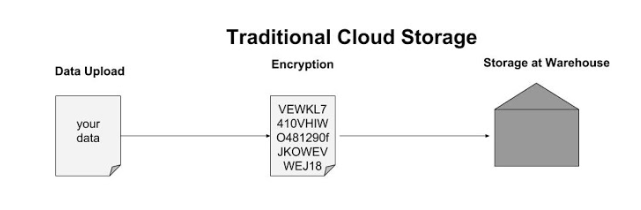
Blockchain cloud storage has two major components: the blockchain technology, which allows the storage to be decentralized and immutable, and the cloud which allows data to be accessible via internet at all times from any device. The combination creates a product which allows data to be stored in distributed locations, where each client and host has equal power to verify a transaction. No central authority has full access to the data, which makes data breaches less likely, whether internal or external.
A Technical Deep Dive
Files are replicated (�redundancy�), broken down into several pieces (�sharding�), translated into an unrecognizable code (�encryption�) and distributed among the storage holders (�decentralization�). A file would have to be found and decrypted at all of its locations in order to be obtained fully. The peer-to-peer framework allows its users to be both client and host at the same time. Users can offer space on their hard drive for others to use and earn the provided currency or pay in order to use more cloud storage than they can provide themselves.
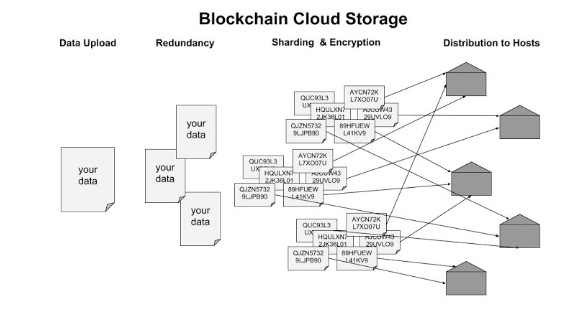
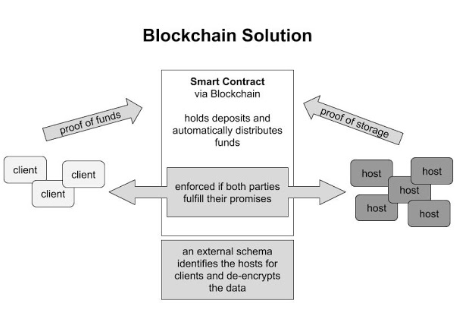
Most of current decentralized cloud storage solutions function on smart contracts. Smart contracts are a blockchain application often used by legal or supply chain providers to enable the automation of fulfilling a contract. Being built into the protocol, they can verify the storage of files of a certain user without a third party and pay or not pay the users depending on whether they fulfilled their duty. The value that is being exchanged usually takes the form of a token, that in most cases is - but does not have to be - a cryptocurrency coin attached to the storage provider. The cryptocurrency may provide an attractive investment add-on to the feature but is in and of itself not necessary for a decentralized cloud storage to function. A value representation is necessary to quantify the value of providing and using storage, but this can be done via tokens only.
Current Market and Players
The market for cloud storage has a current compound annual growth rate of 23.7%, but cybercrime costs are growing at 30% with a current costs of $750 billion. The blockchain�s main advantage lies in providing secure storage, as it becomes more difficult to hack multiple partitioned and distributed encrypted files, as opposed to centralized providers that are easier hackable from inside or outside. The largest players in the field are Storj, Sia, FileCoin and MaidSafe, with Storj and Sia being in the market for the longest, but FileCoin joining with a strong ICO and MaidSafe interrupting with powerful security implementations.
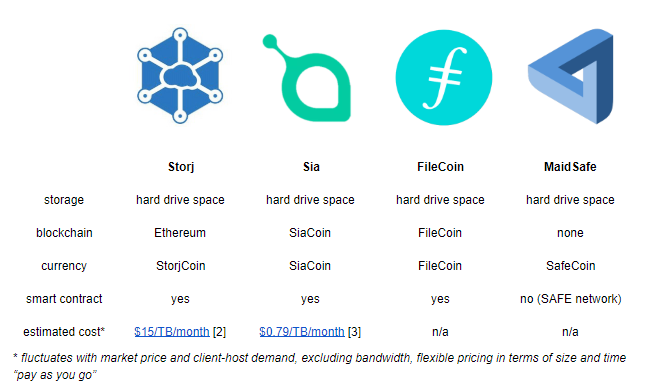
Traditional Cloud Storage Costs
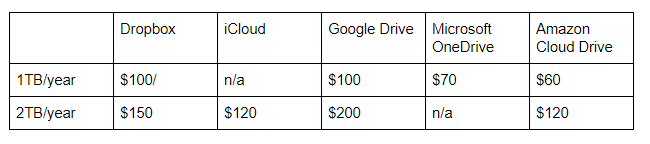
Shortcomings and Solutions
Current limitations include scalability, as start-ups must find ways to manage the distribution and discovery of large amounts of data. Additionally, users have to have their hard drive continuously available, meaning both connected to power and the internet. If that is the case, a replication of files ensures that users have access to their files even when single hard drives are inaccessible. Cost and earnings are market dependent. In general, the more storage hosts provide and the longer their computer is turned on, the more they can earn. This may be profitable for someone with free storage and electricity, but could end up costly for those who have to make investments for such. Additionally, as hosts get paid via internal currency, the exchange rate of the currency will also determine the final value of their investment.Data security concerns arise from attacks on the entire network or on individual nodes or hosts. In network wide 51% hacks, 51% of blockchain nodes agree as a majority on a decision for the entire network, which can be done via high computational efforts. In Distributed Denial of Service (DDoS) hacks the network is overloaded by traffic, which delays the completion of requests. The hosts� security operations in place depend on the hosts themselves - a central feature of decentralization, but a vulnerability to the safety of data. Nonetheless, as files are encrypted and distributed, hacking single pieces of files will not result in a detrimental data breach, and hacking all files at all locations is close to impossible[5].Anna Pauxberger contributed to this report. Sources[1]Annual number of data breaches and exposed records in the United States from 2005 to 2017 (in millions) (2018), https://www.statista.com/statistics/273550/data-breaches-recorded-in-the-united-states-by-number-of-breaches-and-records-exposed/ (last visited July 02, 2018).[2]Myles Snider, The State of Decentralized Storage (2017), https://multicoin.capital/2017/09/27/state-decentralized-storage/ (last visited July 02, 2018)[3]storage marketplace/ storage pricing (2018), https://siastats.info/storage_pricing (last visited July 02, 2018)[4]Brian Barrett, Amazon Just Killed The Best Deal In Tech (2017), https://www.wired.com/story/amazon-just-killed-the-best-deal-in-tech/ (last visited July 02, 2018)[5]Sia Tech, Addressing Thoughtful Concerns about Sia�s Security + Viability (2017), https://blog.sia.tech/addressing-thoughtful-concerns-about-sias-security-viability-103ccfff5e92 (last visited July 02, 2018)
.png)



.png.png)